Hiding Malicious Programs In a Computer’s Uefi Firmware, the deep-seated code that instructs a PC on how to launch its operating system, has become a nasty tactic in the toolbox of stealthy hackers.
When a motherboard maker puts its own covert backdoor in the BIOS of millions of computers—and fails to secure that hidden backdoor—they are effectively doing hackers’ work for them.
Researchers at the firmware-focused cybersecurity firm Eclypsium stated today that they identified a secret mechanism in the firmware of Gigabyte motherboards, whose components are extensively used in gaming PCs and other high-performance machines. Eclypsium discovered that whenever a computer with the affected Gigabyte motherboard restarts, code within the motherboard’s firmware covertly initiates an updater program that runs on the computer and downloads and executes another piece of software.

While Eclypsium claims the hidden code is intended to be a harmless utility for updating the motherboard’s firmware, researchers discovered that it is constructed insecurely, potentially allowing the process to be hijacked and used to install malware instead of Gigabyte’s intended software. Because the updater program is initiated by the computer’s firmware rather than the operating system, it is difficult for users to remove or even detect.
“If you have one of these machines, you have to worry about the fact that it’s basically grabbing something from the internet and running it without you being involved, and it hasn’t done any of this securely,” says Eclypsium’s strategy and research lead, John Loucaides. “Most people don’t like the idea of going underneath the end user and taking over their machine.”
Eclypsium listed 271 Gigabyte motherboard types that researchers think are affected in a blog post regarding the research. Users who want to see which motherboard their computer is using can do so by heading to “Start” in Windows and then “System Information.”
Related: North Korean Hackers Are Attacking US Hospitals
Eclypsium claims to have discovered Gigabyte’s hidden firmware mechanism while searching customers’ machines for firmware-based malicious programs, a tactic increasingly used by sophisticated hackers. For example, in 2018, hackers working for Russia’s GRU military intelligence agency were caught stealthily installing the firmware-based anti-theft software LoJack on victims’ computers as an eavesdropping method. Two years later, Chinese state-sponsored hackers were found repurposing a firmware-based spyware tool developed by the hacker-for-hire firm Hacking Team to target the computers of diplomats and non-governmental organization workers in Africa, Asia, and Europe. The researchers at Eclypsium were astonished to find that their automatic detection scans flagged Gigabyte’s updater mechanism for engaging in some of the same dubious behavior as other state-sponsored hacking tools—hiding in firmware and surreptitiously installing a software that downloads code from the internet.
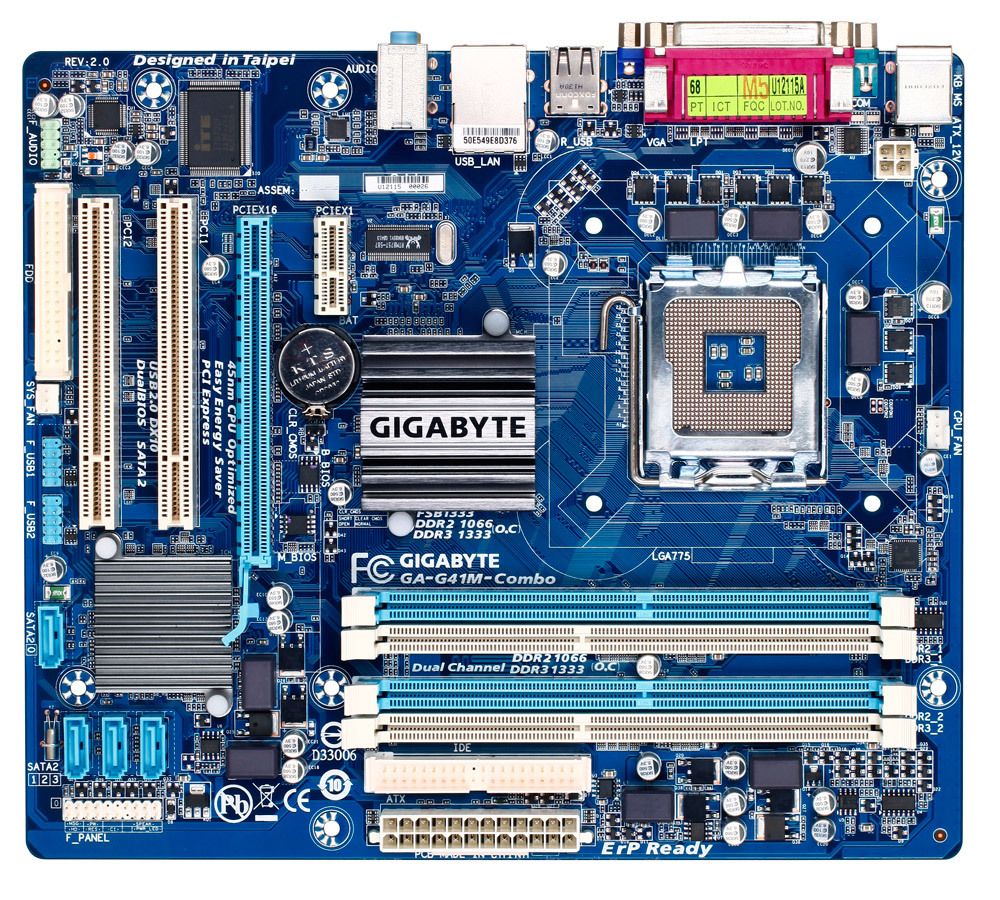
Users who don’t trust Gigabyte to silently install code on their machine with a nearly invisible tool—or who are concerned that Gigabyte’s mechanism could be exploited by hackers who compromise the motherboard manufacturer to exploit its hidden access in a software supply chain attack—might be concerned by Gigabyte’s updater alone. However, Eclypsium discovered that the update mechanism was constructed with obvious flaws that could allow it to be hijacked: It downloads code to the user’s machine without properly authenticating it, and in certain cases does so through an unprotected HTTP connection rather than HTTPS. This would allow a man-in-the-middle attack carried out by anyone who can intercept the user’s internet connection, such as a rogue Wi-Fi network, to impersonate the installation source.
In other cases, the updater installed by Gigabyte’s firmware mechanism is configured to be downloaded from a local network-attached storage device (NAS), a feature that appears to be designed for business networks to administer updates without all of their machines connecting to the internet. However, Eclypsium advises that in such instances, a malicious actor on the same network could impersonate the NAS’s location in order to install their own malware surreptitiously.
Eclypsium claims to have been working with Gigabyte to report its results to the motherboard maker, and that Gigabyte has stated that it intends to solve the problems.

Even if Gigabyte releases a fix for its firmware issue—after all, the issue stems from a Gigabyte tool designed to automate firmware updates—Eclypsium’s Loucaides notes that firmware updates frequently fail silently on users’ machines, owing to their complexity and the difficulty of matching firmware and hardware. “I still believe this will be a fairly widespread problem on Gigabyte boards for years to come,” Loucaides says.
Eclypsium’s discovery is “troubling,” says Rich Smith, the chief security officer of supply-chain-focused cybersecurity company Crash Override, given the millions of possibly compromised devices. Smith has written about firmware vulnerabilities and has analyzed Eclypsium’s results. He compares the scenario to the mid-2000s Sony rootkit affair. Sony had concealed digital-rights-management code on CDs that installed itself invisibly on consumers’ computers, creating a vulnerability that hackers exploited to hide their virus. “You can use techniques that have traditionally been used by malicious actors, but that wasn’t acceptable, it crossed the line,” Smith adds. “I can’t speak to why Gigabyte chose this method of software delivery.” But it appears to me that this crosses a similar line in the firmware space.”
Smith admits that Gigabyte’s hidden firmware tool had no harmful or deceptive purpose. However, leaving security flaws in the invisible code that lurks beneath the operating system of so many computers undermines a basic layer of trust that users have in their equipment. “There is no intention here, only sloppiness.” “However, I don’t want sloppy coders writing my firmware,” Smith explains. “You’re building your house on sand if you don’t trust your firmware.”
Download The Radiant App To Start Watching!
Web: Watch Now
LGTV™: Download
ROKU™: Download
XBox™: Download
Samsung TV™: Download
Amazon Fire TV™: Download
Android TV™: Download