Mac malware expert Patrick Wardle is well recognized, but he had no idea how far his work had spread.
He is the founder of the Objective-See Foundation, a nonprofit that develops open-source security technologies for macOS, and a former employee of the NSA and NASA. Since Wardle is now playing this latter position, a large portion of his software code is now openly available for download and decompilation; part of this code has reportedly gained the attention of tech businesses who are exploiting it without his consent.
Thursday at the Black Hat cybersecurity conference, Wardle and Tom McGuire, a cybersecurity researcher at Johns Hopkins University, will present their case. The researchers discovered that code created by Wardle and made available as open source throughout the years made its way into several commercial products — all without the users giving him credit or purchasing a license to utilize the work.
The issue, according to Wardle, is that it’s challenging to demonstrate that the code was stolen rather than accidentally built in a comparable manner. Fortunately, Wardle was able to make more progress than most because of his expertise with reverse-engineering software.
In a chat with The Verge before to the talk, Wardle said, “I was only able to figure [the code theft] out because I both develop tools and reverse engineer software, which is not super common.” “I could detect it occurring to my tools since I cross both of these disciplines, but other independent devs might not be able to, which is the issue,” the developer said.
The thefts serve as a reminder of how vulnerable open-source programming is, which powers a large section of the internet. There are minimal safeguards against dishonest developers who choose to take advantage of open-source developers as the code is frequently already public. Open-source developers typically make their work available under particular licensing conditions. In one recent instance, the founder of the open-source Mastodon project filed a legal complaint alleging that the Donald Trump-backed Truth Social app had copied major amounts of code.
The software program OverSight, which Wardle released in 2016, is one of the key instances in his case. With great success, Oversight was created to check whether any macOS applications were secretly accessing the microphone or webcam. It was useful for finding Mac malware that was spying on users as well as for revealing the fact that a legitimate program like Shazam was constantly listening in the background.
Wardle, whose cousin Josh Wardle developed the well-known Wordle game, claims he constructed OverSight because a Mac user couldn’t easily verify which applications were activating the recording hardware at a given time, particularly if the applications were made to operate covertly. His software uses a variety of unconventional and consequently one-of-a-kind analysis techniques to overcome this difficulty.
Years after Oversight’s release, he was shocked to see that some commercial programs used identical application logic in their own goods, down to copying Wardle’s code’s faults.
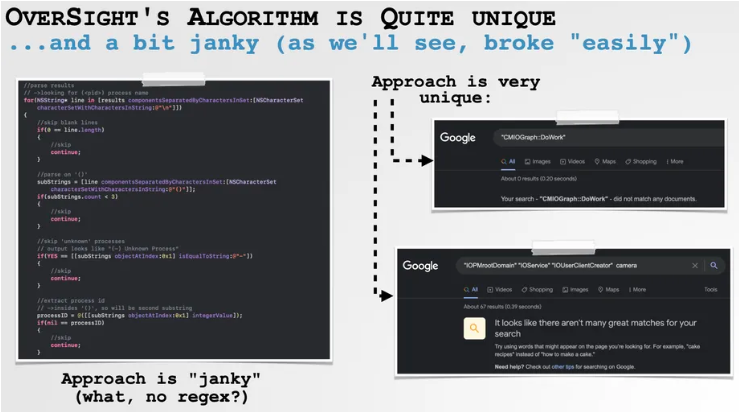
It was discovered that three distinct businesses had used methods taken from Wardle’s work in their own commercially available software. In the Black Hat session, none of the responsible firms are mentioned since, according to Wardle, the code theft was probably the work of a single employee rather than the result of a top-down plan.
When asked about it, the businesses also responded favorably, according to Wardle: all three vendors he approached apparently acknowledged using his code without permission in their goods and all finally paid him directly or sent money to the Objective-See Foundation.
Code theft is an awful fact, but Wardle intends to assist developers and businesses safeguard their interests by raising awareness of it. He recommends software engineers to learn how to use tools that can help them find instances where theft has happened and to write code (whether open source or closed source) with the expectation that it will be stolen.
He advises businesses to properly inform staff members on the legal guidelines governing the practice of commercially exploiting the reverse engineering of another product. Finally, he just wants them to stop stealing.

